Hard to
believe it but Facebook has only just
turned 12, meaning it is still young enough to have not been around
at the turn of the millennium. Yet, it’s true. As its co-founder Mark
Zuckerberg will tell you, it came into existence on February 4th, 2004.
It’s funny,
because, as one of the biggest and most successful brands in the world, it
feels like it has been around for a lot longer, as if it were around before
even the internet came into popular use. Needless to say, that would be
impossible.
And anyways,
its rapid ascent is indicative of the kind of world we now live in. This is the
21st century, after all, where new technologies can disrupt the status-quo
faster than lightening. It’s amazing what is now possible. Facebook, not even a
teenager, has already conquered the world … well, at least socially.
In this
timely guide, we look at five of the best ways that you, one of Facebook’s 1.2
billion plus active users – a number that goes to show its universal appeal –
can keep on enjoying the engaging, connective and transformative service it
offers.
Why is this
important? Because it’s an important part of our daily lives, a network that
allows direct access to our most personal of experiences. It needs to be respected
and, moreover, protected.
Sadly, while
the service has gone from strength to strength over the years, running parallel
to this has been the evolving threat of cybercrime, which is fast becoming “the crime of our generation”. The threat remains very real,
both externally and internally (Facebook isn’t without its own flaws).
While the
tech giant knows this and regularly updates its website – at the end of last year it introduced a new security checkup for Android, as a
case in point – part of the responsibility in remaining secure lies with its
users. Below is a guide helping you stay protected.
1.
Constructing a near-impenetrable password is a must
If your
password is weak – and for many people, this is highly likely – then you are offering cybercriminals
an opportunity to access your account with very little effort or expertise.
Make your
Facebook password original – different to the ones you have on other, online
accounts – and complex. This includes using, for example, capitals, numbers and
symbols, making spelling mistakes and using cryptographic solutions … from an 11-year-old.
2.
Knowing where you are logged in at all times
Technology
has evolved to allow us to be connected to our Facebook account at all times
and on multiple devices at the same time. However, keeping track of which
computer, tablet or smartphone we are actually logged into can be difficult.
Luckily, the
company has developed a solution to this. Facebook records every logged in
account as an active session, which you can see and manage under security
settings. You can also end sessions from here. Note: smartphone logins can
sometimes show an unusual location because your device may have connected through
cell towers outside your usual area.
3.
Switch on login alerts to spot unauthorized access
Facebook
allows you to set up login alerts, which means that every time someone logs
into your account from a different computer or smartphone, you will be
notified. This means that if someone other than yourself has accessed your account you can swiftly
deal with it.
The process
that follows any unauthorized use of your account is fairly robust. For
example, the social media giant will take you through a step-by-step
authentication process, establishing what changes were or were not made by you.
4.
How not to get caught by a phishing hoax
Along with
spam, discussed below, phishing scams are ubiquitous on social media.
Problematically, as ESET’s David Harley has previously observed, they have become
“markedly more sophisticated”.
One of the
most common types of scams used on Facebook is a spoof login page that looks
like it’s the real deal. It’s used to uncover your unique username and password
combination. Again, trust your intuition – if it looks odd or has come out of
the blue, be wary. The same applies for so-called official requests for credit
card details. As with banks, the tech firm will never request this information
this way.
5.
Dealing with the longstanding problem of spam
Spam is
a problem we can all do without, yet, unfortunately, it has a way of rearing
its ugly head every now and again. It can come in multiple forms on Facebook –
masked as a friend or family request, a post and even a message.
If you have
any doubts about the authenticity of something, then be cautious. Instead of
clicking onto it – or sharing it – report it (as spam). Interestingly, if you
notice, for example, that a friend or family member’s account is repeatedly
sharing spam, you can message them to “resolve this” issue.







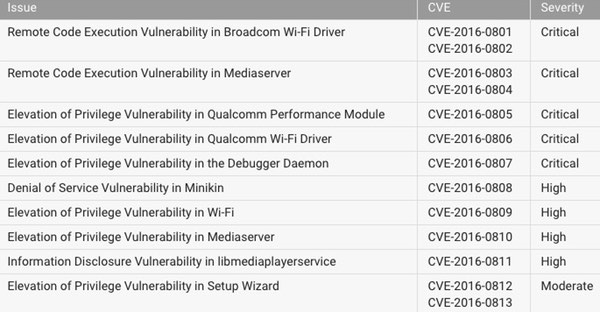
 But remember this – these are flaws in Android, and the Nexus is just one brand of Android smartphone.
But remember this – these are flaws in Android, and the Nexus is just one brand of Android smartphone.